
Unpatchable? How Chinese Hackers Hid in Dell VMs for 2 Years Using "Magic Packets"
A deep dive into the critical Dell 0-day. How Chinese hackers used "Ghost NICs" and invisible malware to hide in corporate networks.
Imagine locking your front door with the most expensive, heavy-duty biometric lock money can buy. You feel safe. You sleep soundly. But you don’t realize that the builder of the house glued a spare key under the doormat—and didn't tell you.
For thousands of organizations running critical virtual infrastructure, that is not a metaphor. It is reality.
On Tuesday, security researchers disclosed CVE-2026-22769, a vulnerability with the maximum possible severity score of CVSS 10.0. For nearly two years, a sophisticated Chinese state-sponsored hacking group known as UNC6201 has been using this flaw to inhabit Dell RecoverPoint for Virtual Machines appliances.
This isn't a simple "smash and grab" data breach. It is a masterclass in persistence. The attackers are using "Ghost NICs" to bypass firewalls and "Magic Packets" to make their backdoors invisible to scanners.
If you are a CISO, a network engineer, or just a cybersecurity enthusiast, you need to understand the mechanics of this attack. Here is the deep dive into how UNC6201 turned Dell servers into invisible fortresses.
Part 1: The "Open Door" Mistake
Despite the sophisticated tradecraft used later in the attack, the initial entry point was shockingly elementary. It stems from a failure in configuration management within the Dell appliance.
Dell RecoverPoint utilizes Apache Tomcat—a widely used open-source web server—to manage its interface. Deep inside the file system of the appliance, located at /home/kos/tomcat9/tomcat-users.xml, researchers found a critical error: Hardcoded Administrator Credentials.
This means that every single unpatched instance of this appliance, globally, shared the exact same username and password for the Tomcat Manager.
The Attack Chain:
- Reconnaissance: Attackers scan the internet for the specific digital fingerprint of a Dell RecoverPoint appliance.
- Access: They log in remotely using the static, default credentials found in the XML file.
- Deployment: They abuse the
/manager/text/deployendpoint. This is a legitimate feature allowing admins to upload Java applications. - Execution: The attackers upload a malicious
.WAR(Web Archive) file containing SLAYSTYLE, a "web shell" that gives them instant Root-level control over the operating system.
But gaining access was just the beginning. The goal was to stay hidden.
Part 2: The Evolution of Malware (JIT vs. AOT)
Once inside, UNC6201 needed to deploy a permanent backdoor. This highlights a fascinating evolution in how state-sponsored hackers are avoiding detection.
For years, this group relied on a malware family called BRICKSTORM. It was written in programming languages like Go or Rust. While powerful, these languages produce large file sizes and leave specific "signatures" that modern Endpoint Detection and Response (EDR) tools can easily spot.
In late 2025, the group shifted tactics. They deployed a new backdoor: GRIMBOLT.
The "AOT" Advantage
GRIMBOLT is written in C#, but it uses a compilation method called Native AOT (Ahead-of-Time). To understand why this is dangerous, we need to look at how computers usually read code.
The JIT (Just-In-Time) Method: Normally, C# code is compiled into an "Intermediate Language." When you run the program, the computer translates it into machine code while it is running (Just-In-Time). Security tools act like a censor standing next to the translator—they watch the translation happen and can spot malicious commands as they are spoken.
The AOT (Ahead-of-Time) Method: GRIMBOLT is different. The attackers compile it directly into machine code before putting it on the victim's server. They strip away the metadata and "intermediate" language. When the malware runs, there is no translation process for the security tools to inspect. It looks just like a native system process.
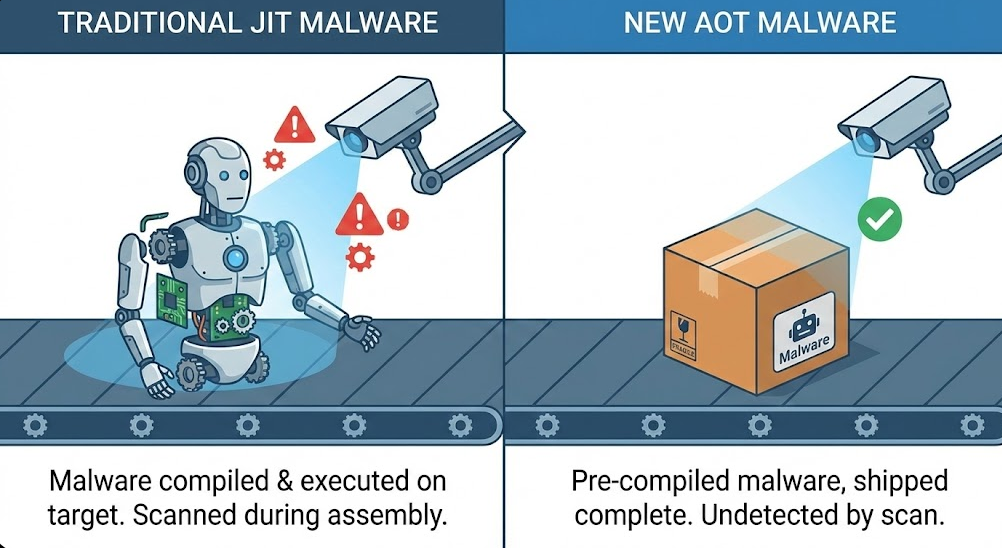 AOT compilation allows malware to arrive pre-packaged, bypassing the runtime analysis that catches traditional .NET malware
AOT compilation allows malware to arrive pre-packaged, bypassing the runtime analysis that catches traditional .NET malware
Part 3: The "Ghost NIC" Phenomenon
Most hackers try to hide their tracks within the Operating System (deleting logs, hiding files). UNC6201 went a layer deeper: The Virtualization Layer.
Because the compromised Dell appliance runs on VMware ESXi, the attackers utilized the underlying infrastructure to create "Ghost NICs."
What is a Ghost NIC?
A Network Interface Card (NIC) is the component that connects a computer to a network. In a virtual environment, you can add as many NICs as you want.
The attackers used their root access to hot-plug a new, virtual network adapter to the infected machine.
- The Visible Path: The legitimate NIC connects to the corporate network, which is heavily monitored by firewalls and logs.
- The Ghost Path: The malicious NIC is bridged to a separate VLAN or directly to the internet, bypassing the corporate firewall entirely.
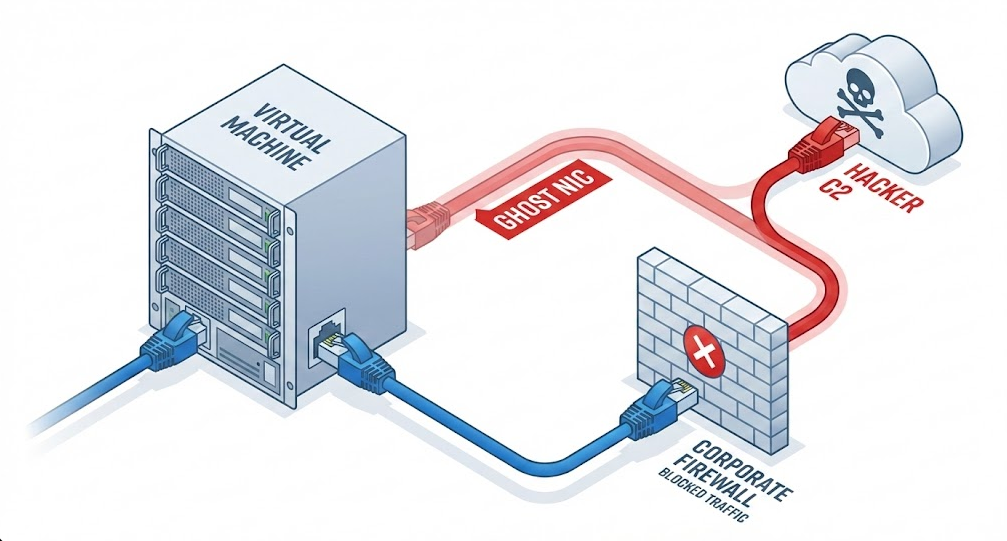 By attaching a secondary virtual network interface, attackers create a direct tunnel to their Command & Control servers, bypassing corporate firewalls
By attaching a secondary virtual network interface, attackers create a direct tunnel to their Command & Control servers, bypassing corporate firewalls
This is the digital equivalent of digging a tunnel out of a bank vault directly to the sewers. The guards at the front door (the Firewall) see nothing leaving the building, yet data is being exfiltrated constantly.
Part 4: The "Magic Packet" (Single Packet Authorization)
Even with a Ghost NIC, the attackers face a problem: Open ports.
If they leave a listening port (like 10443) open for their backdoor, a security scanner (like Shodan or a corporate Nmap scan) will eventually find it. An open port on a critical server is a red flag.
To solve this, UNC6201 implemented Single Packet Authorization (SPA), utilizing a technique often referred to as "Port Knocking" or "Magic Packets."
How the Secret Knock Works
The malware modifies the server's iptables (the Linux firewall) to DROP all traffic destined for their backdoor port (10443). To the outside world, the port appears dead.
However, the malware also installs a "sniffer" that watches traffic hitting the standard HTTPS port (443). It is looking for a specific, hardcoded sequence of data—a hexadecimal string.
- The Knock: The hacker sends a packet to Port 443 containing the "Magic String."
- The Validation: The sniffer sees the string and identifies the hacker's IP address.
- The Gate: The malware dynamically updates the firewall rules to ALLOW traffic from only that hacker's IP to Port 10443.
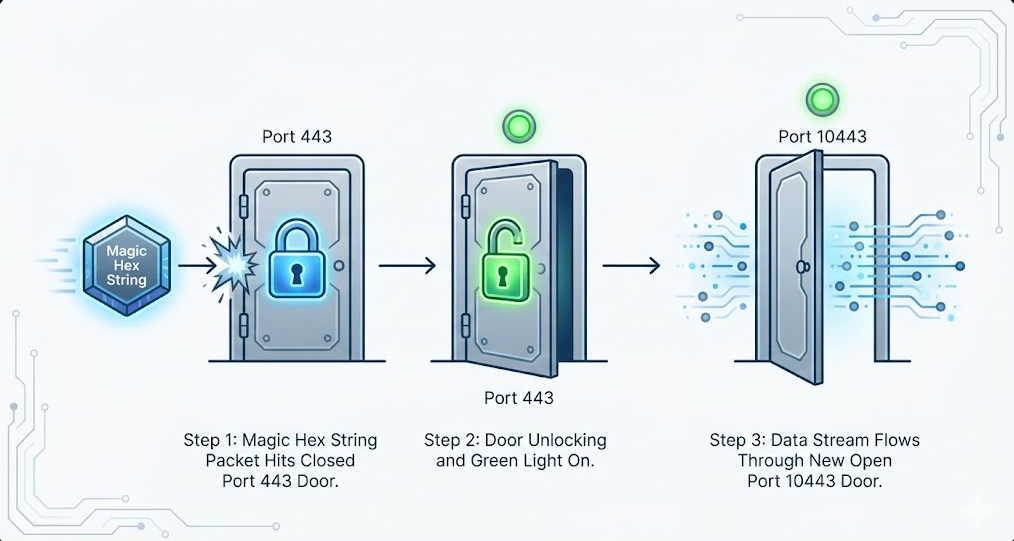 The backdoor port (10443) remains invisible until a specific 'Magic Packet' is received on Port 443, triggering the firewall to open momentarily.
The backdoor port (10443) remains invisible until a specific 'Magic Packet' is received on Port 443, triggering the firewall to open momentarily.
This technique renders the backdoor invisible to automated scanners. Unless you know the secret knock, the door simply doesn't exist.
Part 5: Intelligence Analysis & The Missing Malware
As a researcher, one of the most telling signs of a sophisticated attack is what you can't find.
I analyzed the Indicators of Compromise (IOCs) provided in the disclosure against public threat repositories like MalwareBazaar. The results paint a clear picture of how targeted this campaign is.
The "Old Guard" (BRICKSTORM)
The older malware samples, identified as BRICKSTORM, are present in the database. These samples (hashes starting with 2388... and 320a...) are tagged as ELF, Linux, and UNC5221. They represent the previous phase of the operation—noisy, Go/Rust binaries that have since been burned.
 Older Brickstorm samples are well-documented in public repositories.
Older Brickstorm samples are well-documented in public repositories.
The "New Ghost" (GRIMBOLT)
However, when searching for the new GRIMBOLT hashes (such as 24a11...), the repositories are empty.
The absence of these hashes in public databases confirms that GRIMBOLT is not being sprayed across the internet. It is a surgical tool, used only on high-value targets, and its AOT compilation/UPX packing is successfully preventing automated sandboxes from analyzing it and sharing the data.
Part 6: The Hunter's List (Indicators of Compromise)
If you are a defender, rely on these indicators. Do not assume your endpoint protection caught this.
Malware: GRIMBOLT (The New, Stealthy Backdoor)
Note: These hashes are currently missing from most public repositories.
SHA256:
24a11a26a2586f4fba7bfe89df2e21a0809ad85069e442da98c37c4add369a0c(Filename: support) SHA256:dfb37247d12351ef9708cb6631ce2d7017897503657c6b882a711c0da8a9a591(Filename: out_elf_2)
Malware: SLAYSTYLE (The Web Shell)
SHA256:
92fb4ad6dee9362d0596fda7bbcfe1ba353f812ea801d1870e37bfc6376e624a(Filename: default_jsp.java)
Malware: BRICKSTORM (The Legacy Backdoor)
SHA256:
aa688682d44f0c6b0ed7f30b981a609100107f2d414a3a6e5808671b112d1878SHA256:2388ed7aee0b6b392778e8f9e98871c06499f476c9e7eae6ca0916f827fe65df(Filename: splisten) SHA256:320a0b5d4900697e125cebb5ff03dee7368f8f087db1c1570b0b62f5a986d759SHA256:90b760ed1d0dcb3ef0f2b6d6195c9d852bcb65eca293578982a8c4b64f51b035SHA256:45313a6745803a7f57ff35f5397fdf117eaec008a76417e6e2ac8a6280f7d830
Network Indicators
C2 IP:
149.248.11.71C2 Endpoint:wss://149.248.11.71/rest/apisession
Behavioral Hunting
Persistence: Check
/etc/rc.localfor any reference toconvert_hosts.sh. Network: Look for unexpected virtual network adapters attached to VMs in ESXi logs.
Part 7: Remediation
If you manage Dell RecoverPoint infrastructure, the time to act is now.
Immediate Patching:
- Version 5.3: Upgrade to 6.0 SP3, then upgrade to 6.0.3.1 HF1.
- Version 6.0: Apply remediation script DSA-2026-079.
The Bottom Line
CVE-2026-22769 is a reminder that the most dangerous vulnerabilities often aren't complex code injection attacks—they are simple configuration errors. A hardcoded password opened the door, but it was the advanced tradecraft of UNC6201 that allowed them to live in the walls for two years undetected.
Stay vigilant, and check your edge appliances today.