
The Invisible Siege: Why Modern APTs Have Weaponized the Operating System
The era of "smash-and-grab" malware attacks is fading among state-sponsored actors. Today’s Advanced Persistent Threats (APTs) have shifted toward a "Living-off-the-Land" (LotL) paradigm.
The era of "smash-and-grab" malware attacks is fading among state-sponsored actors. Today’s Advanced Persistent Threats (APTs) have shifted toward a "Living-off-the-Land" (LotL) paradigm. By utilizing legitimate system administration tools—PowerShell, WMI, and LOLBins—attackers blend into the background noise of enterprise networks, rendering signature-based detection obsolete and turning the defender’s own infrastructure into a weapon.
 A visualization of the 'Living-off-the-Land' paradigm. Rather than introducing foreign code, attackers subvert legitimate operating system components—represented here as the internal mechanics of the OS—to dismantle security controls from the inside.
A visualization of the 'Living-off-the-Land' paradigm. Rather than introducing foreign code, attackers subvert legitimate operating system components—represented here as the internal mechanics of the OS—to dismantle security controls from the inside.
I. The Strategic Pivot: Evasion Over Destruction
Historically, an adversary’s greatest liability was their toolkit. Custom malware requires development resources and carries a unique digital fingerprint (hash) that antivirus vendors can blacklist.
Modern APTs, such as APT29 (Nobelium) and the emerging Volt Typhoon, have realized that the most effective camouflage is the system itself. Why compile a malicious binary when certutil.exe can download payloads and PowerShell can execute them in memory?
This shift offers three distinct tactical advantages:
- Attribution Anonymity: When an attack uses standard Windows commands, it becomes difficult to link the activity to a specific nation-state based on code stylometry.
- Signature Evasion: Traditional AV/EPP solutions scan files written to disk. LotL techniques often execute in memory or utilize binaries that are digitally signed by Microsoft.
- Allowlist Bypassing: Application control policies (like AppLocker) usually permit system binaries like
rundll32.exeto run.
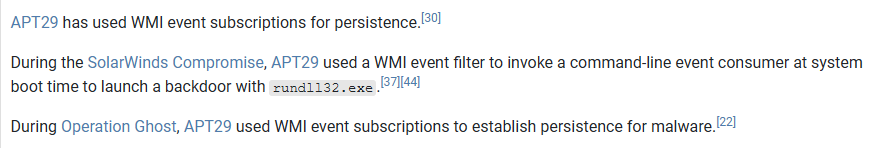 Snippet of APT29 from MITRE Framework
Snippet of APT29 from MITRE Framework
II. The Sword: Weaponized PowerShell
PowerShell is the de facto standard for Windows administration, making it the perfect dual-use technology. For an attacker, it provides full access to the .NET framework and the Windows API without ever dropping a compiled executable.
The Attack Vector
Attackers utilize "Fileless" execution strategies. A typical chain involves a malicious macro spawning a PowerShell process that downloads and executes code directly into RAM.
Key Techniques:
-EncodedCommand: Attackers Base64 encode their scripts to obscure the command line arguments from simple string matching.- Reflective DLL Injection: Loading dynamic link libraries directly from memory, bypassing the Windows image loader.
Real-World Application: APT29 (Cozy Bear)
During the SolarWinds campaign, APT29 utilized heavily obfuscated PowerShell scripts to blend in with legitimate Orion software activity. They leveraged the TEARDROP and RAINDROP loaders to deploy Cobalt Strike beacons, but the initial footholds were often secured and expanded using native PowerShell commands to query Active Directory.
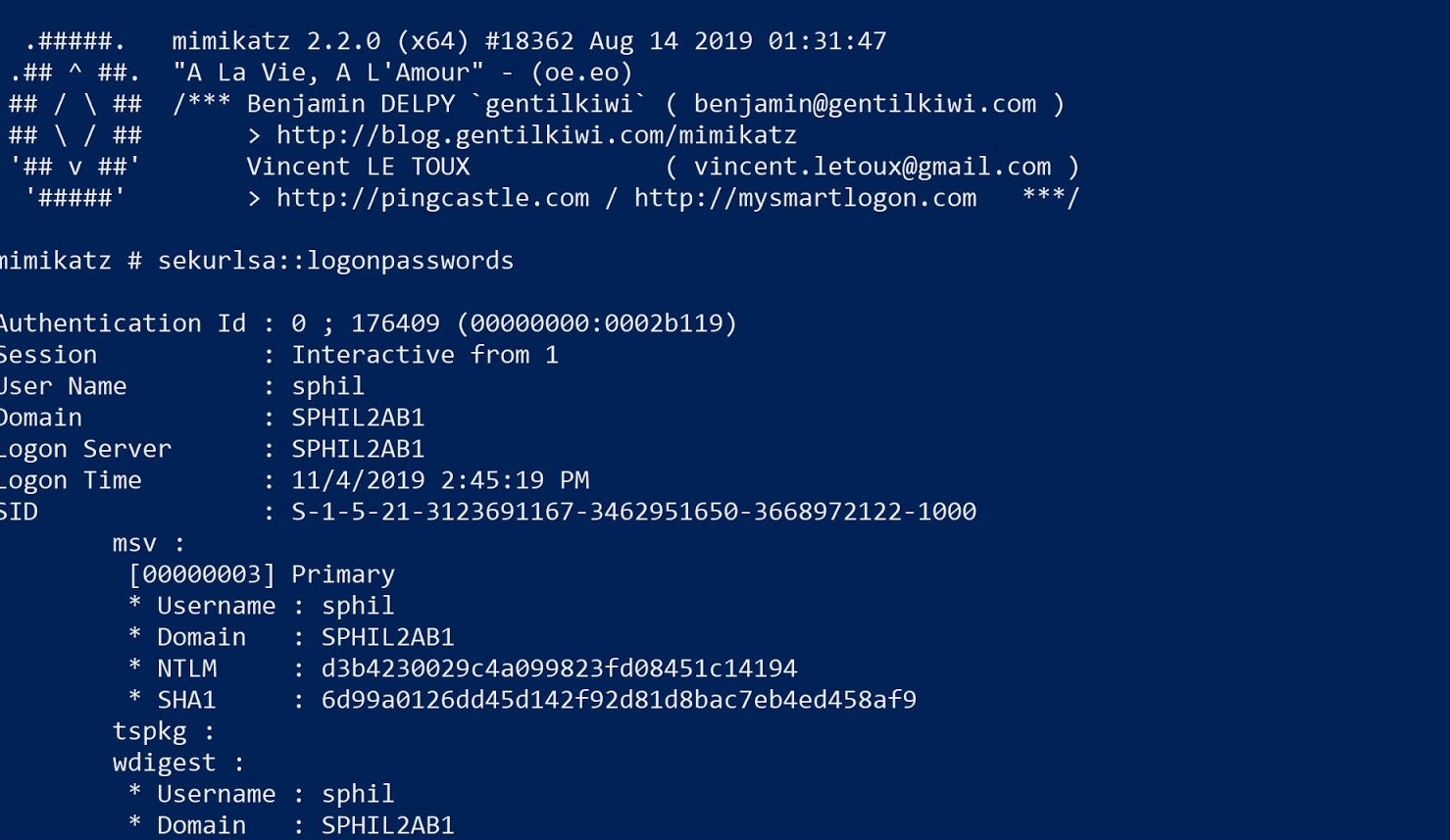 The Anatomy of a Fileless Attack. This screenshot demonstrates a classic PowerShell "Download Cradle." By using IEX (Invoke-Expression) combined with Net.WebClient, the attacker downloads the Mimikatz script and executes it directly in RAM. Note that the malicious binary never touches the disk, bypassing traditional file-based antivirus scanning
The Anatomy of a Fileless Attack. This screenshot demonstrates a classic PowerShell "Download Cradle." By using IEX (Invoke-Expression) combined with Net.WebClient, the attacker downloads the Mimikatz script and executes it directly in RAM. Note that the malicious binary never touches the disk, bypassing traditional file-based antivirus scanning
III. The Ghost: Windows Management Instrumentation (WMI)
If PowerShell is the sword, WMI is the ghost. WMI is the infrastructure for management data and operations on Windows-based operating systems. It is notoriously difficult for defenders to monitor because it is asynchronous and ubiquitous.
The Persistence Mechanism
WMI allows for "subscription-based" persistence. An attacker can configure a WMI Event Consumer to trigger a malicious script only when a specific system event occurs (e.g., system uptime reaches 5 minutes, or a specific user logs in).
- Why it works: The malicious code is stored in the WMI Repository (the CIM database), not as a standalone file like
trojan.exe. - The Blind Spot: Few organizations log WMI activity comprehensively because it generates massive volumes of data.
Real-World Application: APT29 and APT41
APT29 has been documented using WMI Event Filters to establish persistence that survives reboots and avoids Autoruns checks. Similarly, APT41 (Double Dragon) has utilized WMI to execute commands laterally across compromised networks, effectively "teleporting" through the administrative layer of the OS.
IV. The Camouflage: LOLBins (Living-off-the-Land Binaries)
LOLBins are non-malicious binaries provided by the OS that are exploited for criminal purposes. The LOLBAS project currently tracks hundreds of these binaries.
The "Unusual Suspects"
Certutil.exe: Designed to manage certificates, attackers use it to download files from the web (-urlcache -split -f) or decode Base64 payloads hidden in text files.Bitsadmin.exe: Used for Windows updates, abused by attackers to create "jobs" that download malware in the background, even when the network is unstable.Rundll32.exe: Used to run code from DLLs. Attackers use it to execute malicious functions within legitimate DLLs or run JavaScript remotely.
Real-World Application: Volt Typhoon
In 2023, the Chinese state-sponsored actor Volt Typhoon was exposed targeting US critical infrastructure. Their defining characteristic was an almost total reliance on LOLBins to route traffic and execute commands, aiming for "ephemeral" presence that vanished upon reboot, leaving minimal forensic artifacts.
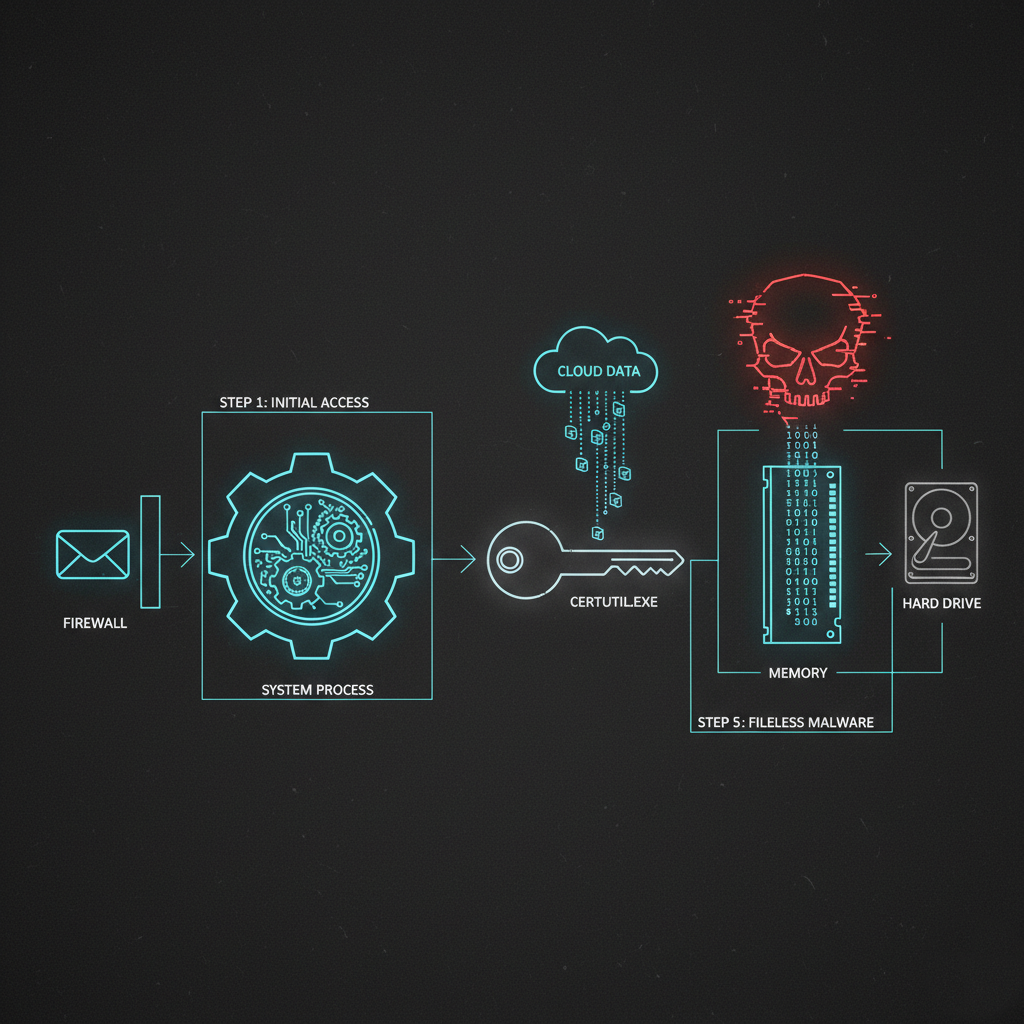 Schematic of a Living-off-the-Land attack vector. Unlike traditional malware campaigns that rely on writing executables to the Hard Drive (Grey), LotL attacks flow from the network directly into System Processes and Memory (Red).
Schematic of a Living-off-the-Land attack vector. Unlike traditional malware campaigns that rely on writing executables to the Hard Drive (Grey), LotL attacks flow from the network directly into System Processes and Memory (Red).
V. The Defender’s Dilemma: Detection Challenges
The preference for LotL creates a severe asymmetry in cyber warfare. Defenders are forced to look for intent, not just content.
1. The Signal-to-Noise Ratio
Blocking PowerShell or WMI is impossible; it would crash the enterprise. SOC analysts are flooded with thousands of legitimate administrative events daily. Distinguishing an admin creating a user from an attacker creating a backdoor requires context that SIEMs often lack.
2. Encryption and Obfuscation
Attackers use PowerShell’s flexibility to XOR encrypt their payloads in real-time. Even if the defender logs the script block, the content may look like gibberish until the millisecond it executes in memory.
3. The "Fileless" Forensic Gap
Traditional Digital Forensics and Incident Response (DFIR) relies on analyzing disk images. When APTs operate exclusively in memory (using WMI and PowerShell reflective injection), a server reboot can destroy the evidence, leaving investigators with no smoking gun.
VI. Conclusion: The Behavior-Based Future
The prevalence of Living-off-the-Land techniques by groups like APT29 dictates a shift in defense strategy. We can no longer rely on "known bad" indicators.
The future of detection lies in Behavioral Analytics and Anomaly Detection. It involves asking different questions:
- Not "Is this file malicious?"
- But "Why is
winword.exespawning a PowerShell child process?" - And "Why is
certutil.exemaking an outbound network connection to an unknown IP?"
Until defenders can master the art of distinguishing the malicious use of benign tools, the operating system will remain the attacker's greatest ally.