
The Notepad++ Hack: A Deep Dive Into a State-Sponsored Supply Chain Attack
How a beloved code editor was turned into a delivery mechanism for sophisticated spyware, and what it teaches us about modern cybersecurity threats.
For millions of developers, IT professionals, and hobbyists, Notepad++ is a trusted, lightweight, and powerful tool. It's the digital equivalent of a reliable Swiss Army knife. But between June and December 2025, that trust was weaponized.
In a sophisticated supply chain attack, state-sponsored hackers compromised the Notepad++ update infrastructure, selectively pushing a malicious backdoor to unsuspecting users. A deep-dive investigation by Rapid7 Labs peeled back the layers of this attack, revealing a custom-built backdoor named "Chrysalis" and the fingerprints of a known Advanced Persistent Threat (APT) group.
Let's break down this complex attack, from the initial breach to the advanced evasion techniques, in a way that everyone can understand.
The Big Picture: What is a Supply Chain Attack?
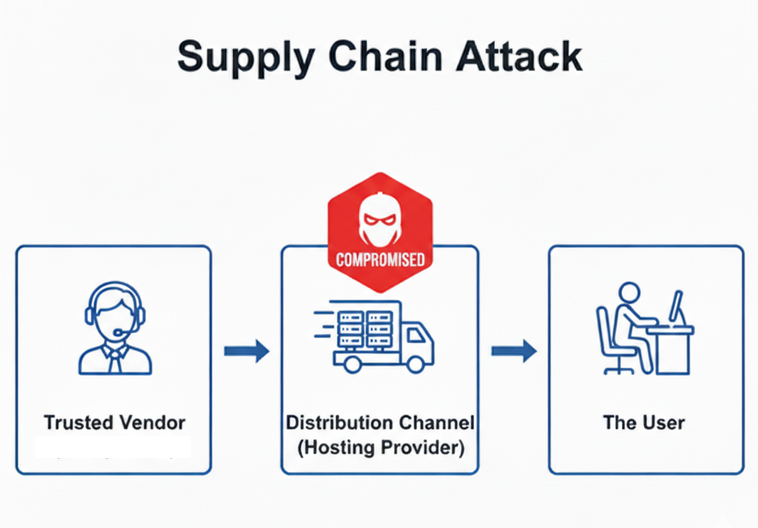 Summary of a Supply Chain Attack
Summary of a Supply Chain Attack
Before we get technical, let's understand the concept. Imagine your favorite restaurant. You trust them to make your food. They, in turn, trust their suppliers to provide safe, high-quality ingredients.
A supply chain attack is like a malicious actor poisoning one of those ingredients before it even gets to the restaurant. The restaurant, unaware, uses the tainted ingredient and serves it to its customers.
In the digital world, Notepad++ was the restaurant, and their web hosting provider was the ingredient supplier. The attackers compromised the supplier to poison the "ingredient" - the software update - before it ever reached the users.
Stage 1: The Lure - Hijacking the Update
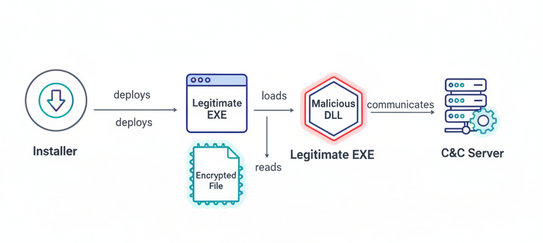 Overview of the Attack
Overview of the Attack
The attack began not with a flaw in Notepad++ itself, but with a compromise of its web hosting provider. This gave the attackers a critical vantage point to intercept update requests.
For Beginners: When a user's Notepad++ checked for an update, the hackers intercepted that request. Instead of sending the real update, they sent a malicious file disguised as the official installer (update.exe).
For the Tech-Savvy: The initial payload was delivered via an NSIS installer. This installer dropped a legitimate, signed Bitdefender binary (BluetoothService.exe) alongside a malicious DLL (log.dll) into a hidden folder.
This set the stage for a classic evasion technique: DLL Sideloading. When the legitimate Bitdefender executable ran, Windows loaded the attacker's malicious log.dll from the same directory instead of the real one, giving the attackers code execution under the guise of a trusted application.
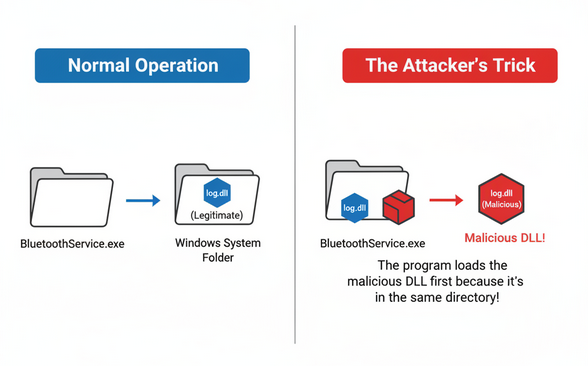 SideLoading DLL Attack
SideLoading DLL Attack
Stage 2: The Weapon - The "Chrysalis" Backdoor
Once the malicious log.dll was running, its main job was to decrypt and unleash the primary payload: a powerful, custom-built backdoor Rapid7 named Chrysalis.
This wasn't just a simple virus; it was a full-featured espionage tool.
For Beginners: Chrysalis acted as the hacker's eyes and ears on the infected computer. It gave them complete control to steal files, run commands, and install more malware, all while remaining hidden.
For the Tech-Savvy: Chrysalis was designed for stealth.
- Encrypted Configuration: It used RC4 to decrypt its configuration, revealing its Command & Control (C2) server:
api.skycloudcenter.com. - Traffic Mimicry: The C2 URL was crafted to mimic the format of a legitimate AI chat service (Deepseek API). This is a clever trick to make its malicious traffic blend in with normal network activity, bypassing many security filters.
- Dynamic API Resolution: Instead of revealing its intentions by directly calling Windows functions, it used API hashing techniques (FNV-1a and MurmurHash variants) to dynamically find the functions it needed at runtime, making static analysis much more difficult.
Chrysalis gave its operators a full suite of capabilities, including an interactive reverse shell, file transfer abilities, and even a self-destruct mechanism to clean up its tracks.
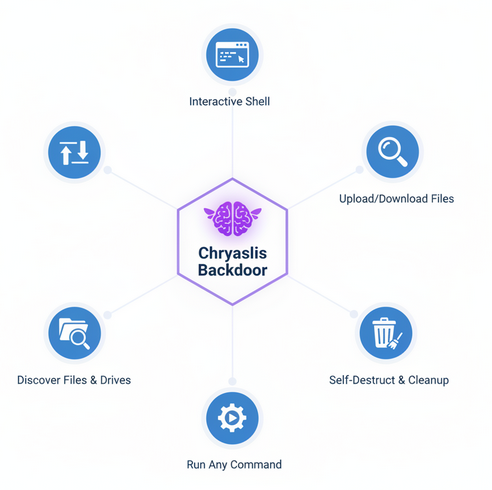 Mind map of Chrysalis backdoor capabilities
Mind map of Chrysalis backdoor capabilities
More than just malware: The 'Chrysalis' backdoor was a fully-featured espionage tool. This mind map shows its key capabilities, giving attackers a Swiss Army knife for controlling the victim's machine.
Stage 3: Expanding the Foothold with Off-the-Shelf Tools
With Chrysalis providing a stable foothold, the attackers didn't stop there. They used their access to deploy even more powerful, commercially available hacking frameworks.
The investigation found evidence of a C source file (conf.c) being used to download and execute a Cobalt Strike beacon. For those unfamiliar, Cobalt Strike is a legitimate (but frequently abused) penetration testing tool that provides powerful post-exploitation capabilities.
This "bring your own tools" approach is common for APTs. They use a custom backdoor for initial access and stealth, then deploy robust, well-known frameworks to carry out their main objectives.
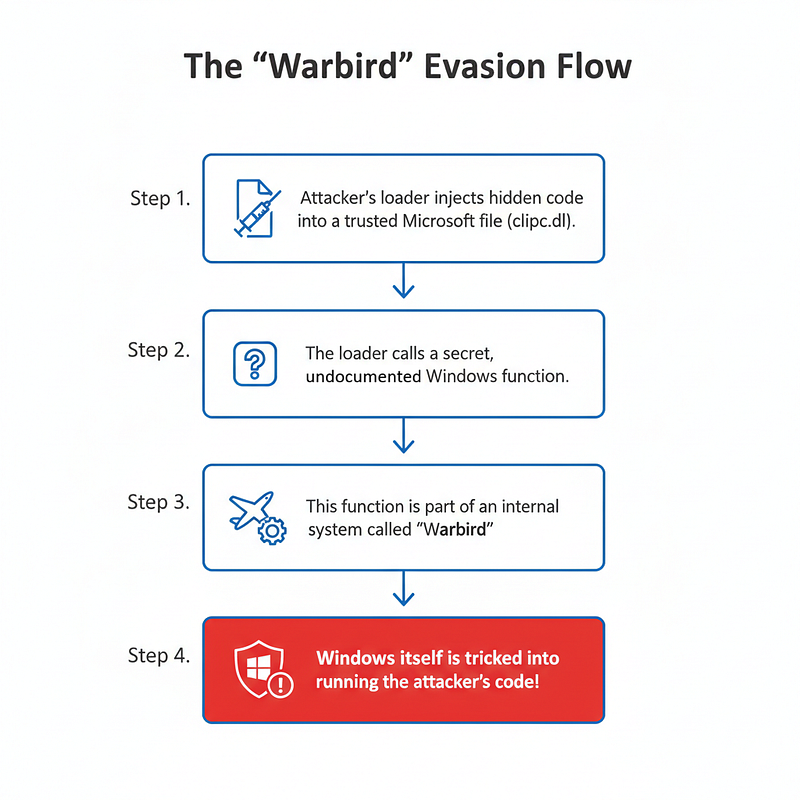
The Masterclass in Evasion: Abusing Microsoft Warbird
 Abusing Microsoft Warbird technique
Abusing Microsoft Warbird technique
The attackers' most advanced trick: Abusing an undocumented Windows feature known as 'Warbird.' This technique allowed them to execute their code from within the memory of a trusted Microsoft file, making it nearly invisible to many security tools.
Perhaps the most fascinating discovery was another loader used by the same group that employed a highly advanced and obscure technique.
For Beginners: The attackers found a way to hide their malicious code inside the memory of a legitimate, Microsoft-signed system file. Think of it as hiding a secret message inside a government-sealed document. It's the last place anyone would think to look, and security software is trained to trust it.
For the Tech-Savvy: This loader, named ConsoleApplication2.exe, used an undocumented Windows function, NtQuerySystemInformation, with a specific information class: SystemCodeFlowTransition (0xB9). This invokes an internal code protection framework known as Microsoft Warbird. By placing their shellcode inside the memory of clipc.dll and calling this function with the WbHeapExecuteCall operation, they could achieve code execution from a context that is almost universally trusted, bypassing many modern security defenses.
Attribution: Who Was Behind This?
 Attribution to Lotus Blossom (Billbug)
Attribution to Lotus Blossom (Billbug)
The attack is attributed with moderate confidence to Lotus Blossom (also known as Billbug), a state-sponsored group with a long history of cyber-espionage. Image from the MITRE ATT&CK® framework.
Rapid7 attributes this campaign with moderate confidence to Lotus Blossom (also known as Billbug or Thrip), a Chinese state-sponsored group known for its cyber-espionage activities targeting government and critical infrastructure sectors. This attribution is based on strong overlaps in tactics, techniques, and procedures (TTPs) with previously documented Lotus Blossom campaigns, particularly the specific method of DLL sideloading.
Key Takeaways
- The Supply Chain is a Major Target: Your security is only as strong as the weakest link in your software supply chain. This attack is a stark reminder that even trusted software can become a threat vector if its distribution channels are compromised.
- Defense in Depth is Crucial: The attackers used multiple layers of evasion (DLL sideloading, API hashing, traffic mimicry, Warbird). No single security tool could have stopped this. A layered defense - combining network monitoring, endpoint detection, and user awareness - is essential.
- Attackers are Innovators: The use of the Warbird framework shows that threat actors are actively researching and weaponizing obscure and undocumented features to stay ahead of defenders.
The Notepad++ incident serves as a powerful case study in the anatomy of a modern cyberattack. It demonstrates a patient, well-resourced adversary willing to combine custom malware with commodity tools and cutting-edge techniques to achieve its goals. For the rest of us, it's a reminder to remain vigilant, question everything, and always, always keep our systems patched.