SOC Analyst Operations Portfolio
Project Overview
Theory is important, but muscle memory saves the day. This portfolio represents 100+ hours of simulated combat against real-world threats.
This repository serves as a comprehensive portfolio of over 100 hands-on security alert investigations conducted on the LetsDefend.io platform.
Unlike a theoretical course, this project demonstrates my practical skills in a simulated, enterprise-grade Security Operations Center (SOC) environment, showcasing a repeatable, professional end-to-end incident analysis workflow.
➡️ View My Verified LetsDefend Transcript
Investigation Categories
The investigations are mirrored after real-world incident tracking systems, classifying threats into specific domains. This demonstrates the ability to identify and triage a wide spectrum of attacks:
- Malware Analysis: Analyzing infections from families like Emotet, Agent Tesla, and Quasar RAT.
- Web Exploitation: Investigating SQL Injection, LFI, and CVE exploitations (e.g., CVE-2023-46214).
- Living off the Land (LOLBins): Detecting malicious use of legitimate binaries like
certutil.exe,mshta.exe, andwscript.exe. - Phishing Response: Triaging credential harvesters, malicious attachments, and "Quishing" (QR Code Phishing).
- Identity Attacks: Analyzing Brute Force attempts against RDP and VPN services, and Privilege Escalation exploits like JuicyPotato.
Performance Metrics
My performance on the platform reflects a high degree of accuracy and commitment to the investigative process.
Success Rate & Accuracy
I have maintained a 95% success rate across all investigated incidents, ensuring that True Positives are correctly escalated and False Positives are closed without disrupting business operations.
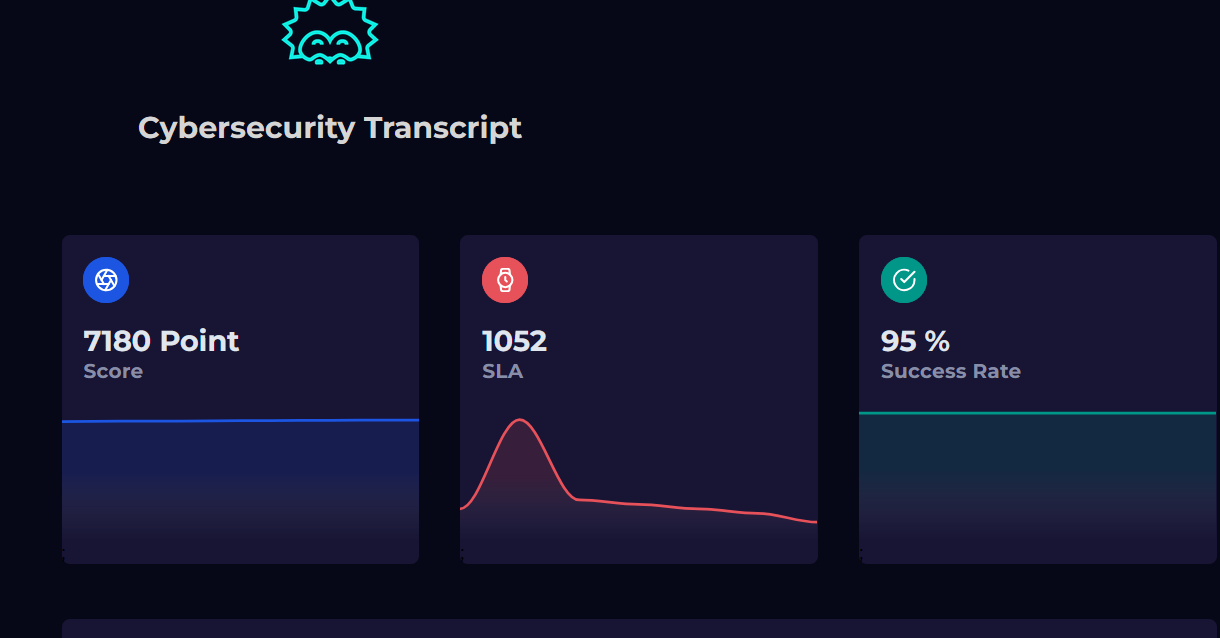 Overall Performance Statistics
Overall Performance Statistics
Consistency Milestones
Security is about consistency. I was awarded the "Non-Stop" badge for sustained investigation efforts and successfully completed the full Security Analyst career path.
 LetsDefend Security Analyst Path Completion
LetsDefend Security Analyst Path Completion
My Investigation Workflow
Each incident in this portfolio follows a structured, NIST-aligned workflow to ensure thoroughness:
- Alert Triage: Rapid assessment of the initial trigger to determine severity and scope.
- Threat Intel Enrichment: Checking IOCs (hashes, IPs, domains) against VirusTotal, AbuseIPDB, and Hybrid-Analysis.
- Log Correlation: Deep-diving into SIEM, EDR, and Network logs to reconstruct the timeline of events.
- Root Cause Analysis: Determining the "Patient Zero" and the initial access vector.
- Reporting: Writing a detailed incident report summarizing findings and providing remediation steps.
Tools Proficiency
The investigations in this portfolio required the operation of a full security stack:
| Category | Tools Used |
|---|---|
| SIEM & Logs | Splunk (Simulated), Windows Event Viewer, Log Management |
| Endpoint (EDR) | Process Tree Analysis, Command Line Auditing |
| Forensics | Wireshark (PCAP), CyberChef (Decoding/Deobfuscation) |
| Threat Intel | VirusTotal, Any.Run, AlienVault OTX |
Verification
This project is a living document of my growth as an analyst. You can view the full repository of reports on my GitHub or verify my badge status below.