CloudLog Sentinel: Cloud-Native SIEM
Project Overview
Modern SOCs drown in noise. The goal of this project was to build a signal-focused detection engine from scratch.
CloudLog Sentinel is a full-stack, cloud-native Security Information and Event Management (SIEM) tool designed to monitor AWS infrastructure in real-time.
Unlike generic logging tools, this application focuses on high-value threat detection, automatically enriching logs with geolocation data to provide immediate context to security analysts.
This project simulates a real-world security monitoring stack, moving raw logs from AWS CloudTrail through a custom Java Spring Boot analysis engine, and finally to a reactive JavaScript dashboard.
Core Architecture
The application relies on a decoupled, microservices-inspired architecture to ensure scalability and separation of concerns.
-
Ingestion: AWS CloudTrail captures audit logs from IAM, EC2, and S3, delivering them to a central S3 bucket.
-
Analysis Engine: The
LogAnalyzerService(Java) polls the bucket on a smart 60-second interval, processing only the current day's logs to prevent latency. -
Enrichment: When a threat is detected, the engine calls the
IpGeolocationServiceto resolve the attacker's IP into a physical location (e.g., "Bengaluru, India"). -
Presentation: A persistent H2 SQL database stores the history, while the frontend polls a REST API (
GET /api/alerts) to update the live dashboard.
Detection Engineering (The 10 Rules)
The engine does not just alert on "errors"; it looks for specific attack patterns based on the MITRE ATT&CK framework. I implemented 10 high-fidelity detection rules:
🔴 Critical Severity
- IAM Admin Escalation: Detects a user attaching the
AdministratorAccesspolicy to a rogue user or role. - S3 Policy Tampering: Detects if an S3 bucket is made public or its ACLs are modified.
- CloudTrail Evasion: Detects attempts to
StopLoggingorDeleteTrailto cover tracks. - Firewall Exposure: Alerts immediately if a Security Group allows
0.0.0.0/0ingress.
🟠 High Severity
- Persistence Mechanisms: Detects the creation of new IAM Users, Access Keys, or Login Profiles (backdoors).
- Secrets Exfiltration: Monitoring for
GetSecretValuecalls to AWS Secrets Manager.
The Dashboard & Visualization
I built a responsive Single Page Application (SPA) using Vanilla JavaScript and Tailwind CSS.
It was designed for "At-a-glance" situational awareness, featuring live-updating stat cards and severity filters.
Main Situational View
The dashboard provides a complete timeline of events. The frontend polls the backend API every 5 seconds, ensuring analysts see threats as they happen without refreshing.
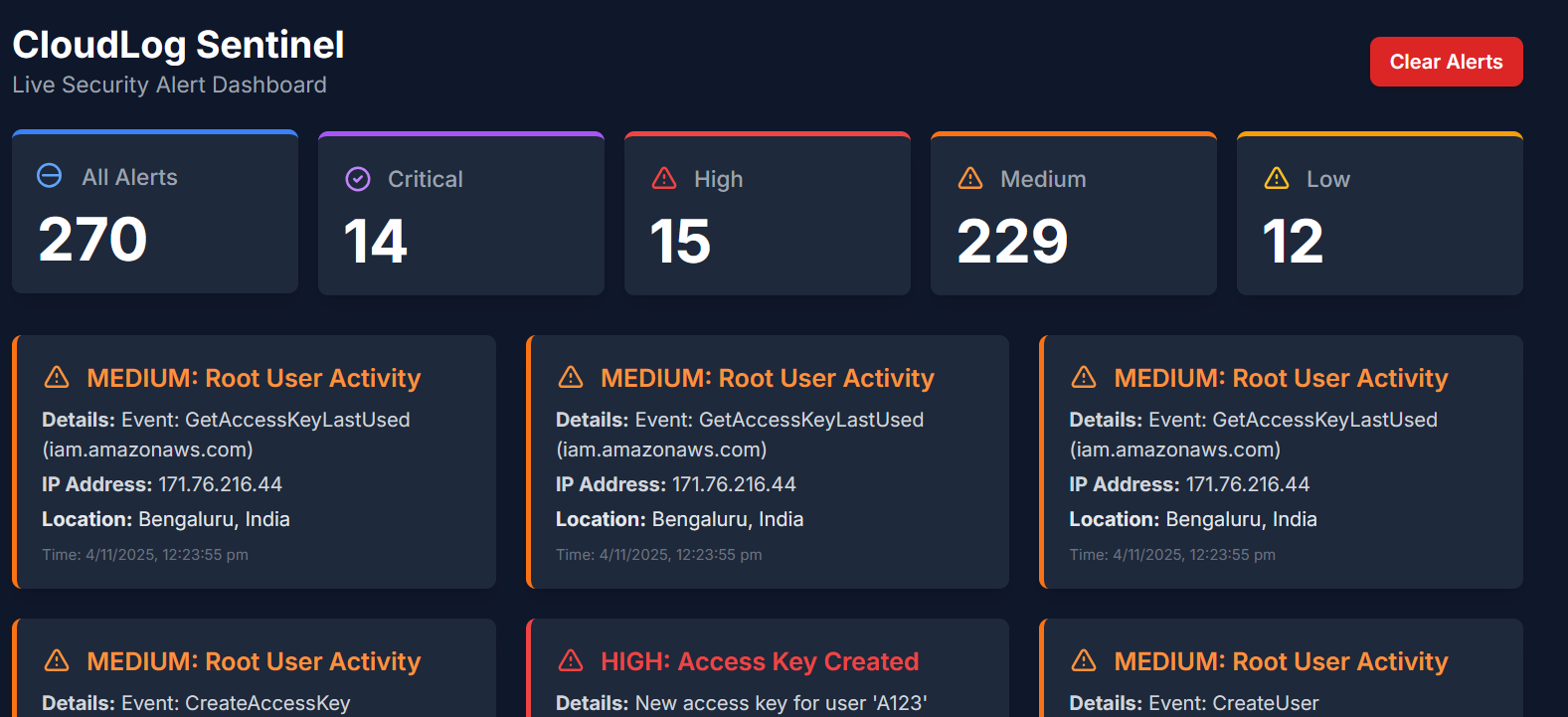 Main Security Dashboard
Main Security Dashboard
Critical Threat Filtering
By toggling the "Critical" filter, analysts can isolate high-priority incidents like Privilege Escalation or Data Exfiltration, removing the noise of failed logins.
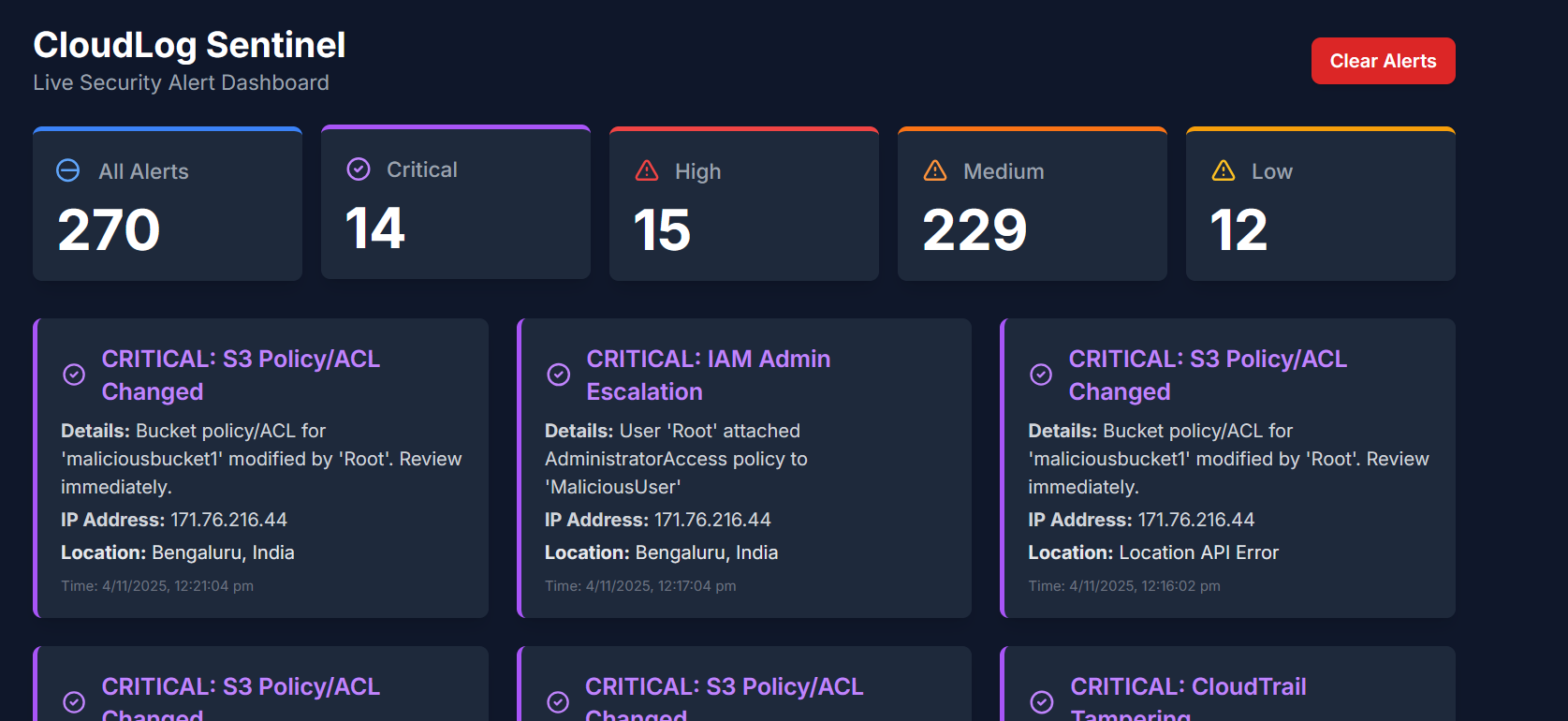 Dashboard filtered to show only Critical Alerts
Dashboard filtered to show only Critical Alerts
Real-Time Alerting
A SIEM is useless if no one watches the screen. I integrated Discord Webhooks to push critical alerts directly to the security team's communication channel.
Each alert is formatted with color-coded embedded messages containing the Source IP, Location, User Identity, and Event Name.
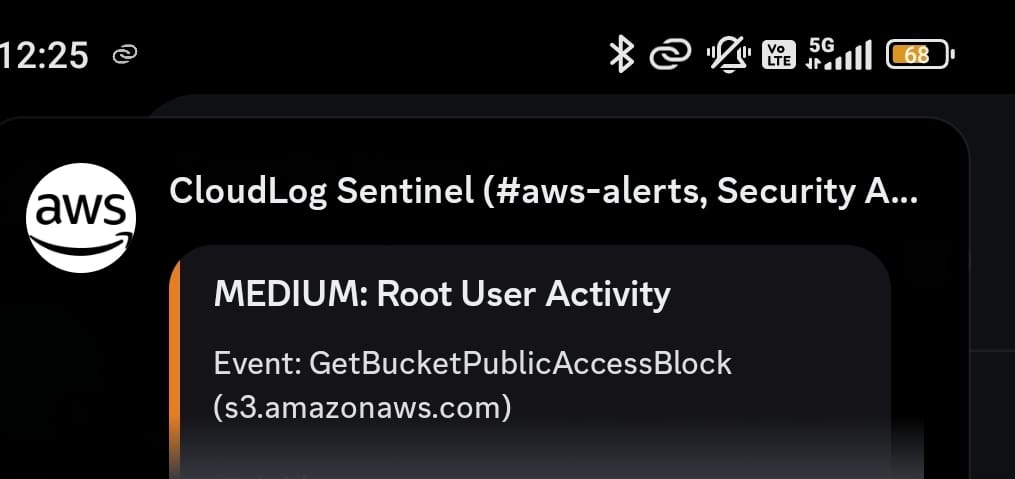 Real-time Discord Push Notification
Real-time Discord Push Notification
Data Persistence & Forensics
To ensure data survives application restarts, I utilized an H2 Database operating in file-based mode.
This allows for historical review and forensic analysis of past alerts via a SQL interface.
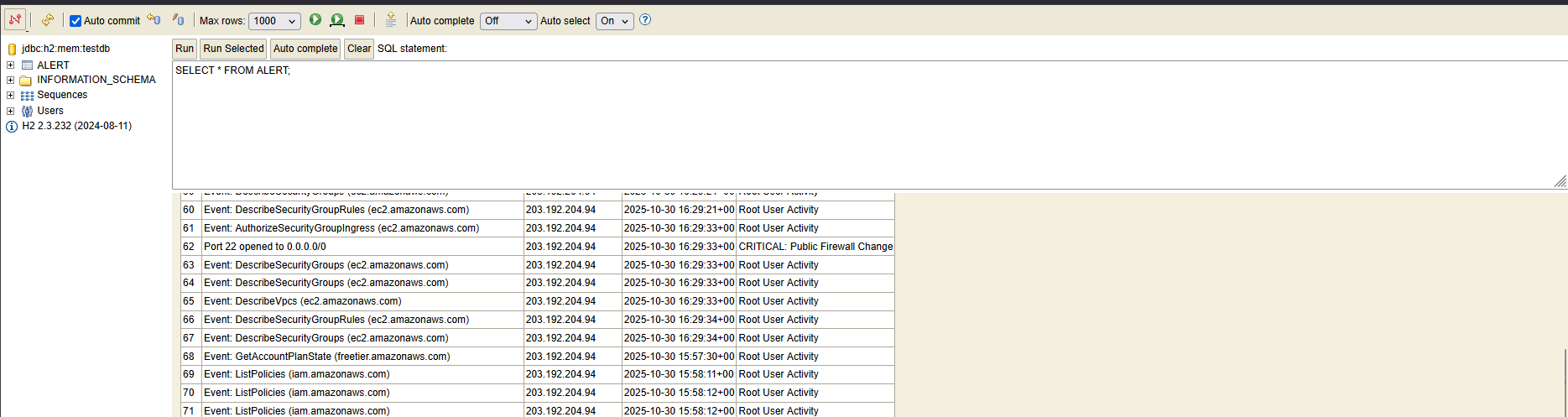 H2 Database Console for SQL Analysis
H2 Database Console for SQL Analysis